CSRF
What Is CSRF?
Cross-Site Request Forgery (CSRF) is a malicious attack tactic that coerces authenticated users into inadvertently carrying out unauthorized actions within a logged-in web application. Once authenticated on a website, users are enticed into performing various actions, such as sending emails/SMS messages, making purchases, or transferring funds, without their explicit consent. Subsequently, the compromised websites execute these actions, often resulting in detrimental consequences for the user.
How Does CSRF Work?
CSRF Attack Process
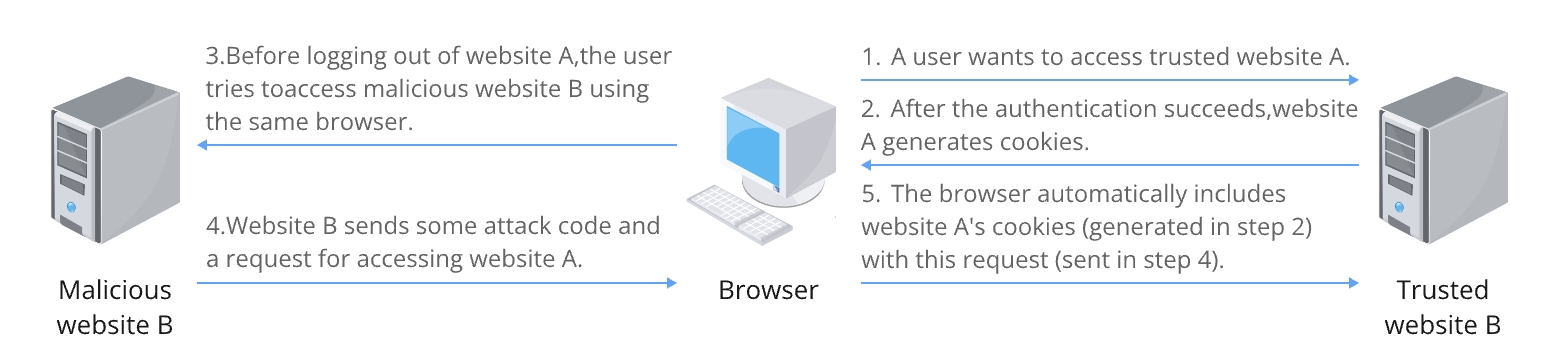
-
1. A user initiates an attempt to access a trusted website A, which has CSRF vulnerabilities, and provides authentication credentials.
-
2. Upon successful authentication, website A generates cookies and transmits them to the browser, completing the login process.
-
3. Before logging out of website A, the user navigates to a malicious website B within the same browser session.
-
4. Website B, upon receiving the user's request, dispatches malicious code along with a forged request to access website A.
-
5. The browser, upon receipt of the attack code, automatically attaches website A's cookies to the request. Unaware that the request originates from website B, website A processes it under the guise of the user's consent based on the provided cookies. Consequently, the malicious code from website B is executed.
In essence, CSRF occurs when an attacker leverages a user's authenticated session to carry out unauthorized actions on a target website.
Defense Policies for CSRF
CSRF attacks typically originate from external websites, posing significant challenges for target websites to fend off. Nonetheless, proactive steps should be taken to bolster the security of vulnerable websites against CSRF attacks.
Verification of the Referer Field in the HTTP Header
By scrutinizing the Referer field in the HTTP header, websites can ascertain the source of resource requests. Alignment of the Referer field with the requesting web page's domain is essential for sensitive data transactions. While this method offers straightforward implementation and enhances security, its efficacy hinges on the browser's adherence to HTTP protocol regulations. Potential vulnerabilities in browsers may compromise the accuracy of Referer field content, rendering it susceptible to tampering after browser compromise.
Adding a token to the request URL and subsequently validating it
The crux of a CSRF attack lies in the deception of users, leading them to unwittingly visit a malicious website. To thwart such attacks, this defense strategy mandates the browser to employ a validation mechanism when users seek access to sensitive data within the browser. This mechanism incorporates a token, typically a piece of data within a form that isn't stored in cookies and remains impervious to forgery by attackers. The server generates a pseudo-random number as the token and appends it to the form. With each request submitted via the form, the client includes this token, which is then authenticated by the server. In normal scenarios, the client browser can accurately retrieve and furnish the token. However, during CSRF attacks, since the token value can't be procured beforehand, it cannot be correctly returned or obtained. Consequently, the request is flagged as suspicious and subsequently rebuffed by the server.
Utilizing verification codes
CSRF attacks instigate network requests devoid of the user's awareness or authorization. Within the verification code mechanism, user interaction with the application is imperative. The server employs the verification code to ascertain whether the request originates from the user deliberately.
You might be interested in
Email Address

-
PoE vs PoE+ vs PoE++ Switch: How to Choose?
Mar 16, 2023








