ECA
What Is ECA?
As the need for securing data and application services intensifies, encryption of traffic for secure communication has become increasingly common. However, while encryption offers a degree of security for communications, it also poses several challenges. The issue arises when malware exploits encrypted channels to initiate network attacks and propagate viruses, with 99% of IT professionals recognizing encrypted traffic as a potential vector for security breaches.
Encrypted Communication Analytics (ECA) is an emerging technique designed to analyze encrypted traffic without the need to decrypt it. ECA employs machine learning algorithms that are trained using initial handshake data, encrypted traffic patterns, and baseline traffic behavior before encryption takes place. It then applies the trained model to categorize and pinpoint malicious activities within encrypted traffic streams. This approach not only preserves user privacy but also equips users with the capability to detect and respond to hidden threats in encrypted traffic promptly, thereby facilitating more effective threat avoidance, prevention, and mitigation.
Why Do We Use ECA?
As digital transformation accelerates, encryption of network traffic has become prevalent to safeguard communication security and user privacy. For instance, the transition from HTTP to HTTPS services reflects this trend. Nonetheless, malicious actors exploit encryption to conceal malware and commands within encrypted traffic, thus eluding detection and enabling the execution of nefarious activities.
The traditional approach to inspecting encrypted traffic involves the use of man-in-the-middle (MITM) techniques, which decrypt the traffic for analysis and then re-encrypt it before forwarding. This method, however, presents several challenges:
1. Employing MITM effectively compromises the very purpose of encryption, which is to protect the privacy of data, and it introduces the potential for compromised channel integrity.
2. As the volume of encrypted traffic continues to grow, the resource-intensive nature of decryption can significantly strain network performance.
Through extensive study of encrypted traffic patterns, researchers have noted marked differences between benign and malicious encrypted traffic originating from both clients and servers. For instance, legitimate traffic often employs up-to-date, robust encryption methods, whereas malicious traffic might rely on older, weaker cryptographic techniques. By leveraging these distinct characteristics, it is feasible to construct machine learning models capable of differentiating between safe and hazardous encrypted communications.
Encrypted Communication Analytics (ECA) emerges as a novel solution, sidestepping the need to decrypt. Instead, it utilizes machine learning to develop a model from pre-encryption handshake data, encrypted traffic metrics, and the broader context of traffic patterns, enabling the classification of encrypted traffic and the identification of potential threats therein. ECA's pivotal role is to detect command and control (C&C) traffic that has been secured using the TLS protocol, thus enhancing security measures without undermining user privacy or network efficiency.
How Does ECA Work?
Encrypted Communication Analytics (ECA) solution is comprised of two main components: the ECA probe and the ECA analysis system. The ECA probe is responsible for capturing and transforming the features of encrypted traffic into metadata, which it then forwards to the ECA analysis model for examination. There are two forms of ECA probes: standalone network probes and those integrated within network switches or firewalls.
At the heart of the ECA solution lies the analysis system is part of the robust HiSec Insight platform. This platform gathers and analyzes various characteristics such as initial handshake data, the temporal relations of data packets, flow metrics, and the broader context within which the encrypted traffic operates. By employing machine learning techniques, the system constructs models that highlight critical features, enabling it to categorize encrypted traffic and effectively pinpoint any malicious content within that traffic. The architecture of this ECA solution is illustrated in the provided diagram.

ECA solution
ECA Process
The Encrypted Communication Analytics (ECA) process for examining encrypted traffic unfolds in three steps, illustrated in an accompanying diagram. Here's an outline of the process:
ECA process
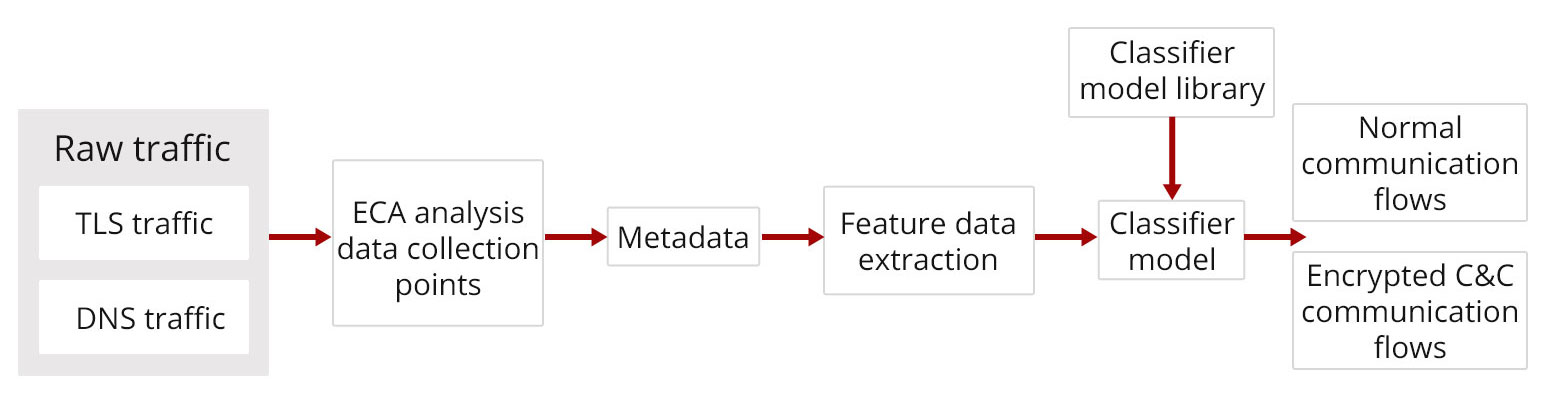
1. Data Labeling and Model Training: The process begins by tagging the data using sets of known malware and benign examples, along with threat intelligence information, such as domain names, IP addresses, and SSL certificate details. Feature vectors are then extracted from several sources: the SSL/TLS handshake between servers and clients, TCP flow statistics, and DNS queries. This includes analyzing signatures from both the client and server sides of the malware and non-malware samples. Utilizing these feature vectors, a machine learning algorithm crafts a classifier model, which serves as the detection engine within the HiSec Insight system.
2. Traffic Feature Extraction: Next, the ECA probes actively extract features from passing encrypted traffic. This includes TLS handshake details, TCP traffic metrics, and DNS/HTTP request information. The probes then transmit this collected data to the HiSec Insight platform for further analysis.
3. Analysis and Detection: Utilizing its big data analytics capabilities, the HiSec Insight system processes the feature data from the ECA probes. The system applies the previously trained ECA detection model to discern potentially malicious command-and-control (C&C) communication within the encrypted traffic. This detection is crucial for uncovering stealthy operations of compromised 'zombie' hosts or identifying advanced persistent threat (APT) attacks during the C&C stage.
You might be interested in
Email Address

-
PoE vs PoE+ vs PoE++ Switch: How to Choose?
Mar 16, 2023








