SYN Flood
What Is SYN Flood?
SYN flood stands out as one of the earliest and most traditional forms of Distributed Denial of Service (DDoS) attacks across the Internet. It exploits the TCP three-way handshake mechanism. Typically, an attacker employs specialized tools or commandeers a network of compromised hosts (zombies) to inundate the target server with an overwhelming volume of TCP SYN packets, each with varying source IP addresses or ports. Upon receiving these packets, the server initiates responses, leading to the creation of numerous half-open connections. As system resources become depleted, the server becomes unable to deliver regular services.
Enhancing server performance and bolstering additional connections is crucial. In the face of massive SYN flood assaults, the key defense strategy lies in discerning authentic connection requests from fraudulent ones and fortifying the shield around legitimate requests, thereby ensuring the processing of normal service requests.
How Does SYN Flood Occur?
SYN flood, as its name suggests, employs a deluge of SYN packets to assault the system. A SYN packet denotes the synchronized packet within the TCP protocol and constitutes the initial step in the TCP three-way handshake process. Below delineates the typical TCP three-way handshake procedure.
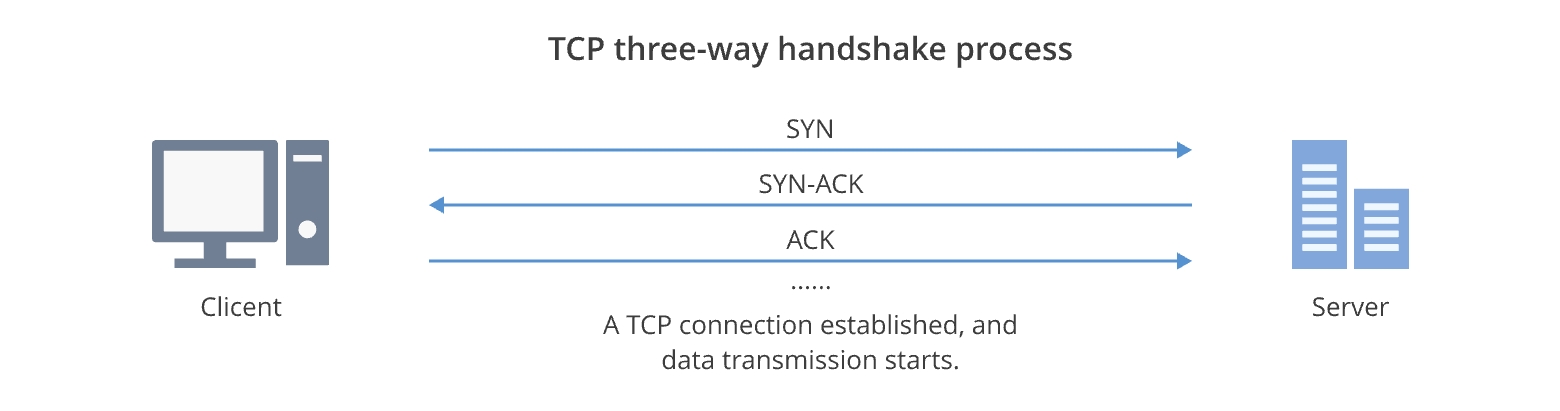
As a connection initiates, the client dispatches a SYN packet to the server and awaits acknowledgment. The source IP address and port number of the SYN packet match those of the client.
Upon receipt of the SYN packet, the server responds with a Synchronize-Acknowledgment (SYN-ACK) packet. The destination address and port number of this SYN-ACK packet correspond to the client's IP address and port number.
Subsequently, upon receiving the SYN-ACK packet from the server, the client dispatches an ACK packet. Upon receipt of this ACK packet, the three-way handshake concludes, establishing the TCP connection.
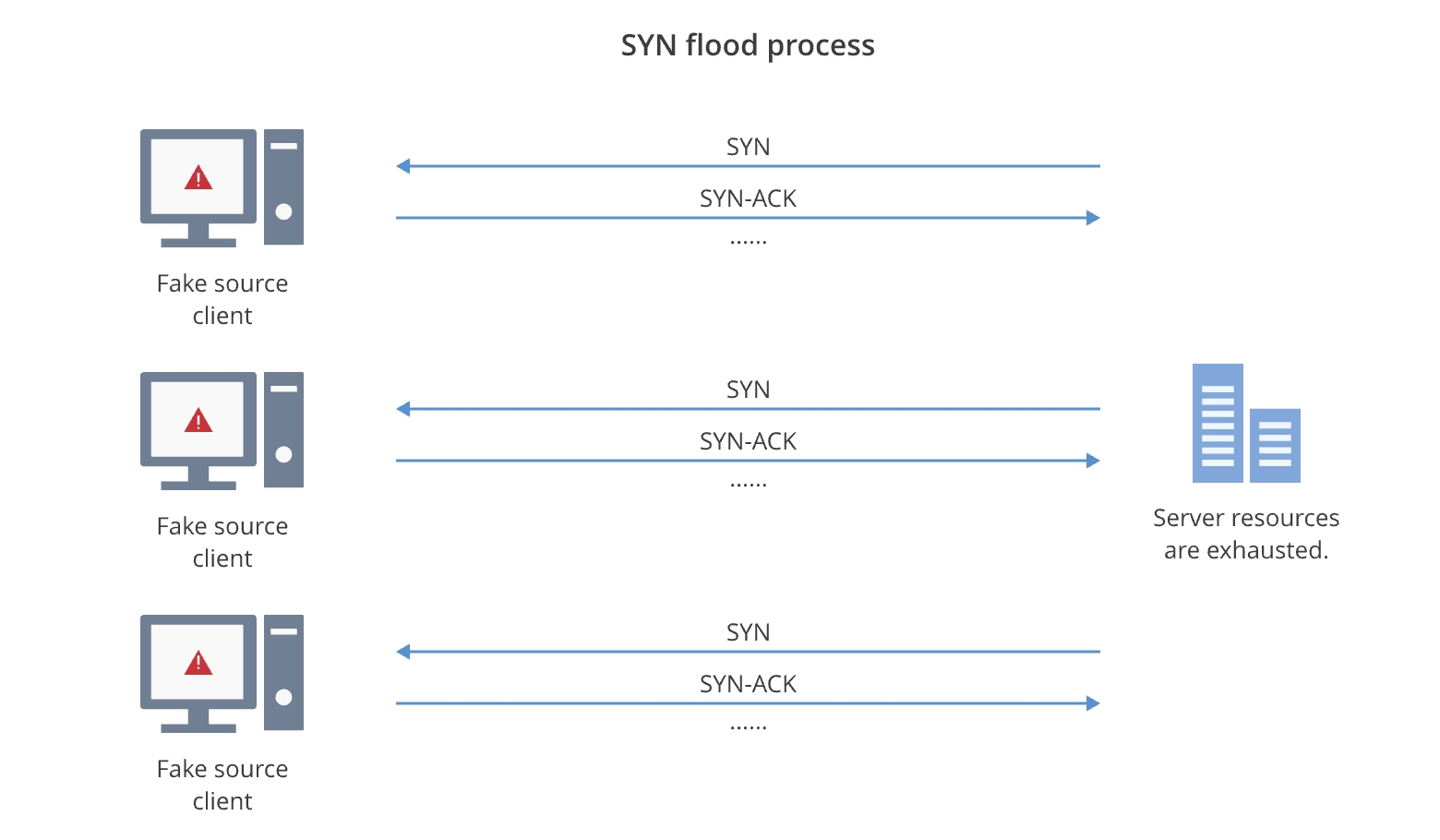
The server remains in a state of anticipation for an ACK packet until the connection times out, constituting a half-open connection. These half-open connections contribute to the server's connection count. Should this count be exhausted, the server's ability to deliver regular services is compromised. Exploiting this mechanism, hackers execute SYN flood attacks.
Typically, hackers inundate the server with a plethora of SYN packets bearing counterfeit source IP addresses or ports, soliciting the establishment of TCP connections. Since these source IP addresses or ports are falsified, the SYN-ACK packets dispatched by the server remain unanswered by the genuine client. In certain instances, hackers opt to utilize authentic source IP addresses to unleash voluminous SYN packets via attack tools. These tools, however, disregard SYN-ACK packets from the server. Consequently, the server fails to receive the ACK packet, resulting in the creation of numerous half-open connections. In such scenarios, the server is compelled to uphold an extensive waiting list while endeavoring to resend SYN-ACK packets, with a multitude of resources remaining unreleased. As these malevolent half-open connections monopolize the server's resources, it becomes incapacitated in responding to fresh SYN packets, thereby thwarting normal users' attempts to establish TCP connections.
How Can We Defend Against SYN Flood?
The objective of a SYN flood attack is to overwhelm server connections and deplete its system resources. For servers, enhancing service capabilities is the primary defense against such attacks, often accomplished through clustering and hardware upgrades. However, this approach incurs substantial costs and offers limited effectiveness against the barrage of attack packets, which can cripple operations within minutes or even seconds.
To thwart such assaults, interception of attack packets before they reach the server is imperative. Security devices like firewalls typically treat SYN packets as standard service packets, necessitating firewall policies to permit their passage for the server to serve external users. Identifying and blocking SYN packets from fake sources via refined security policies is feasible, but predicting and swiftly adjusting to unforeseen attack traffic poses a challenge for administrators.
In such scenarios, deploying an anti-DDoS system becomes essential. Positioned at the network ingress, this system filters SYN packets, identifies fake source IP addresses, shields the server from packets originating from these addresses, and forwards only legitimate SYN packets. The anti-DDoS system employs two primary methods for SYN packet processing: source authentication and first-packet drop.
Source authentication entails the anti-DDoS system responding to a client's SYN packet with a SYN-ACK packet on behalf of the server. Failure of the client to respond marks it as a fake source, while a response from the client whitelists its IP address, allowing SYN packets to pass through for a defined duration without proxy response.
Alternatively, employing a first-packet drop mitigates performance bottlenecks by preemptively discarding the first SYN packet received. Since most SYN flood attack packets alter source IP addresses, the anti-DDoS system perceives all SYN packets as initial packets and discards them outright. Retransmitted SYN packets undergo source authentication, significantly reducing proxy pressure on the anti-DDoS system. This dual approach effectively thwarts SYN flood attacks, particularly those originating from falsified source IP addresses and ports, safeguarding the reliability of the TCP protocol.
You might be interested in
Email Address

-
PoE vs PoE+ vs PoE++ Switch: How to Choose?
Mar 16, 2023








